What is SSL and HTTPS?
To understand SSL and HTTPS you first should understand HTTP, otherwise known as how a web browser communicates with a web server. HTTP is the foundation of the internet and the first thing I encourage to learn more about when asked about web programming. In it's simplest form it's like passing notes in school. Your browser writes a message to the server asking for something, e.g. a web page, along with a few pieces of information known as request headers. This is all done in plain text, meaning anyone who can see it can read it, which is a very real security concern. This can range from innocuous reading of these messages to altering them with a Man in The Middle Attack.
How do we prevent this? By using HTTP over SSL, a.k.a HTTPS. Using our school message passing analogy what this equates to is writing your messages with a secret decoder ring. SSL allows encryption of these messages between your web browser and web server. This is done with an SSL certificate. There are essential two types of these certificates, a self-signed certificate or one issued from a certificate authority.
Self-Signed Certificates
A self-signed certificate is exactly that but a web browser who is trying to authenticate which web server it is communicating with cannot trust a self-signed certificate. An analogy for this would be going to a US bar and when asked for ID presenting one you made your self. This should not work and is potentially illegal. What does a self-signed certificate look like? Well in the Chrome web browser, like this:
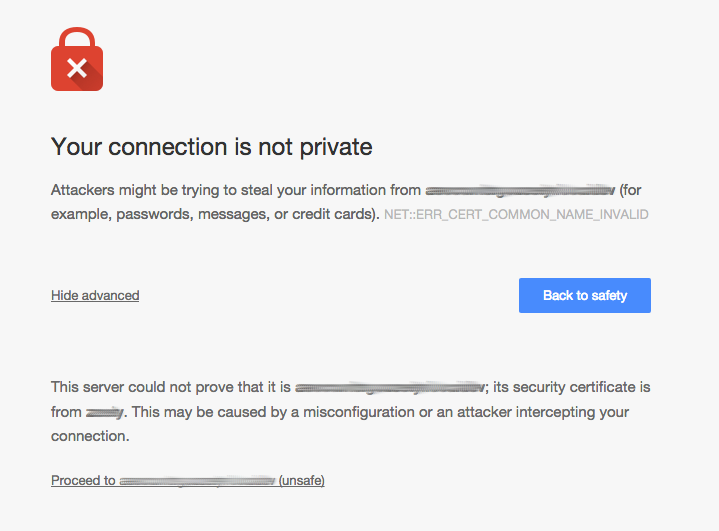
This is a self-signed certificate for my development environment which I use to test our HTTPS configuration. So in this case I'm fully aware that my certificate is self-signed. But if you are seeing this screen for your web site then either you are experiencing an attack or there could be an HTTPS misconfiguration.
Another visual, which you should always look for when making an online purchase, is the web browser address bar. There is a lock icon before the url when on an HTTPS connection. If this is not green you should not be making a purchase. Here is an example of a secure connection versus insecure:
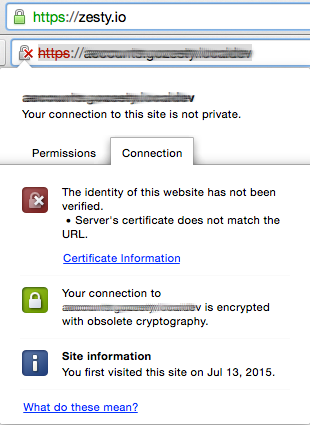
That little red lock icon is the most important reason to ensure you have a properly configured SSL certificate and HTTPS connection.
If I don't see a green lock, I don't buy.
This is my ability to trust your brand when making online purchases or filling out a form. It's importance cannot be understated. There is no room for error here. For example recently Wordpress experienced a global issue when Chrome updated the way it was sending it's HTTPS request headers, due to Apache/PHP variables, this caused login pages to improperly load over HTTPS. This hurts brand trust when users go to visit login pages which are now appearing insecure. I feel the pain of web developers who have to explain how it's not a security issue and figure out work arounds.
Certificate Authorities
So if self-signed certificates are not an option for production websites. What do you use? Just like with your ID in a bar you need a government issued one, i.e. a third party validated ID. This is exactly what an issued certificate from a (CA) certificate authority is. An independent service which verifies your identity and the authenticity of your website. This is what makes it so I cannot steal your certificate and serve it from another web server.
Unfortunately the whole HTTPS process is a little complicated, especially when you start dealing with SSL termination, managing certificates, and sub domains. At Zesty we automate and manage a lot of this away from our customers. And hopefully we will see a large leap forward with the whole process once the EFF's vision for encryption with letsencrypt.org launches.
Why do I need this?
Beyond the practical benefits of security and privacy with communications between your brand website and your customers there are a few more. First and foremost trust! I remember a time when the banking service I used was not using HTTPS with their login pages. Being aware of the security concern I choose not use their online services. It was a major hinderance to getting business done. I feel bad for customers who weren't aware of the security concern.
As a consumer I expect the brands I give my business to handle any personal data, PII, I provide with the utmost care and concern. It's quickly becoming the de facto for any data communication online.
Another benefit is search ranking. Google now factors in HTTPS connections as a rank signal and is actively pushing for HTTPS across the whole web.
What is the cost?
There are a few hard costs when using HTTPS. First there is the obvious purchase of the SSL certificate. This will vary depending upon which certificate authority you purchase from, what type of certificate you choose, and the included warranty. The most important thing here is not the cost but the reputation of the authority your buying from.
Secondly a lot of businesses use other services in between the web browser requesting a web property and a web server. For example DDoS mitigation services, load balancers, and CDNs. Each of these have to be configured to work with your certificate and might have additional costs when using HTTPS.
Cloudflare has a great graphic which demonstrates this.
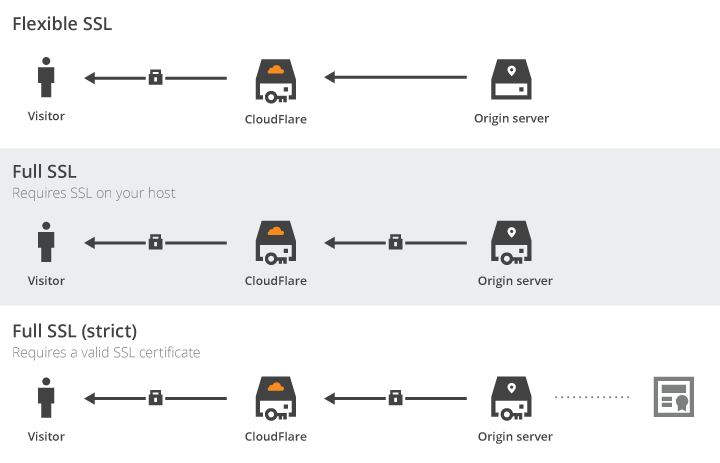
Then there are soft costs. Managing and ensuring your certificates are up to date. Development resources to handle potential configuration issues or patching security vulnerabilities as they are reported. Doing this all over again when it's time to launch another brand web property for your businesses marketing efforts.
How Zesty Helps
At Zesty we handle the development pain of managing all the services necessary to deliver your web properties over HTTPS. When our customers purchase SSL certificates we handle the process of implementing and managing them.